SSO against Cisco Duo Identity Provider
This article describes how to configure Cisco Duo to enable Imagicle users to login to web portal, gadgets and Attendant Console with Single Sign-on based on SAML protocol.
Prerequisites
In order to successfully configure your Cisco Duo, you should have the following data:
User Pool ID
Redirect URI
More details are available here.
Procedure
Login to your DUO admin portal
Select Applications item from the left menu panel
Click on “Protect an Application”
Enter “generic” in the search box
Hit “Protect” button, included in “2FA with SSO hosted by Duo” protection type
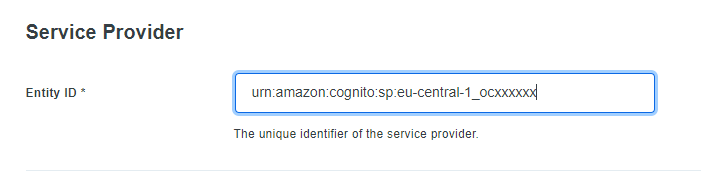
In "Service Provider" section, please enter the User Pool ID in the "Entity ID" field. See below:
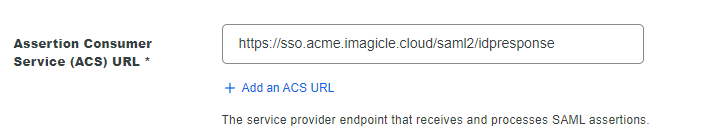
In the “Assertion Consumer Service (ACS) URL” field, please enter the Redirect URI. See below:
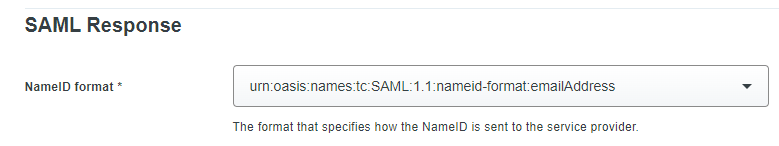
In "SAML Response" section, enter the NameID format corresponding to an email address. See below:
In NameId attribute, please select "Email Address". See below:
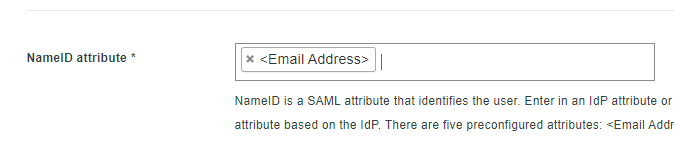
In the Map Attributes section, configure a map for the <Email address> attribute to be mapped into the SAML Response attribute “http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress”
See the following picture:
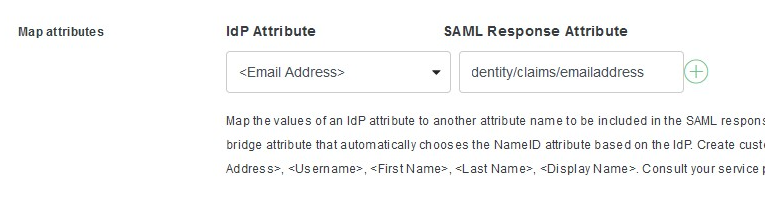
In “Settings” section, enter the Name "Imagicle SSO" to identify Imagicle applications. See below:
Hit “Save”
Click on “Download XML” button:
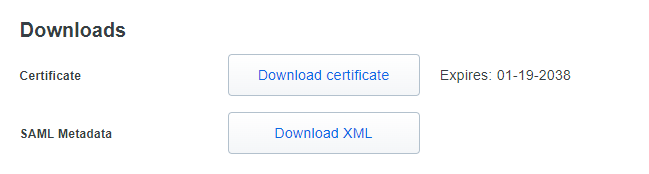
Please send downloaded file to Imagicle Team to complete the SSO federation.
