FortiOS 6.4.4 > ikev2 (static)
Configuring Fortinet Next Generation Firewall
Version tested: Fortinet Next Generation Firewall version FortiOS 7.2
In this section we will refer to the configuration file you obtained from our UCCS Onboarding teams as “template conf” and will explain how to use its contents for configuring FortiOS 7.2.
As a reference for this guide, here is the full AWS file: FortiOS 6.4.4+ ikev2 (static).txt
Interface names in AWS template are too long and need to be adjusted.
Create VPN Tunnels
To create VPN Tunnels go to VPN > IPSec Tunnels > click “Create New”
The VPN Creation Wizard appears, select “Custom” and click Next:
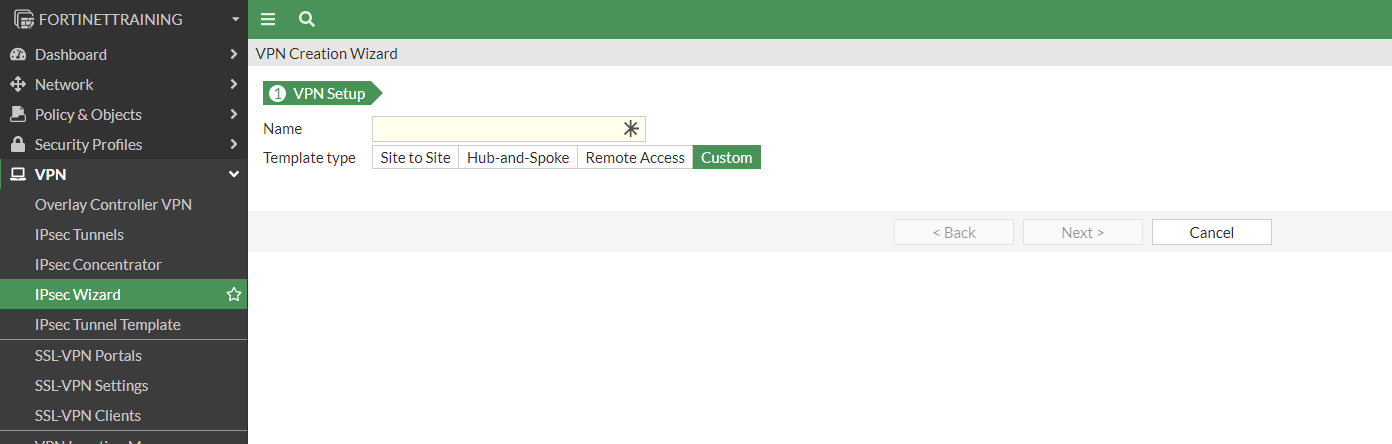
Configure the tunnel as specified in the template conf #1 Internet Key Exchange (IKE) Configuration
a. IP Version: IPv4b. Remote Gateway: Static IP Addressc. IP address: 18.198.85.36d. Local Interface: wan1e. Local Gateway: Select Specify and enter WAN port IP (Public IP)f. Dead Peer Detection: Enable by selecting On Idle/ On Demandg. Authentication Method: Pre-shared Keyh. Pre-Shared Key: zyLuRLk01w_VENyShLKTF2qoocnuIPSmi. IKE Version: 2Phase 1 Proposal:j. Encryption: aes128k. Authentication: sha1l. DH group: 2 ! and deselect 5m. Keylife: 28800 seconds
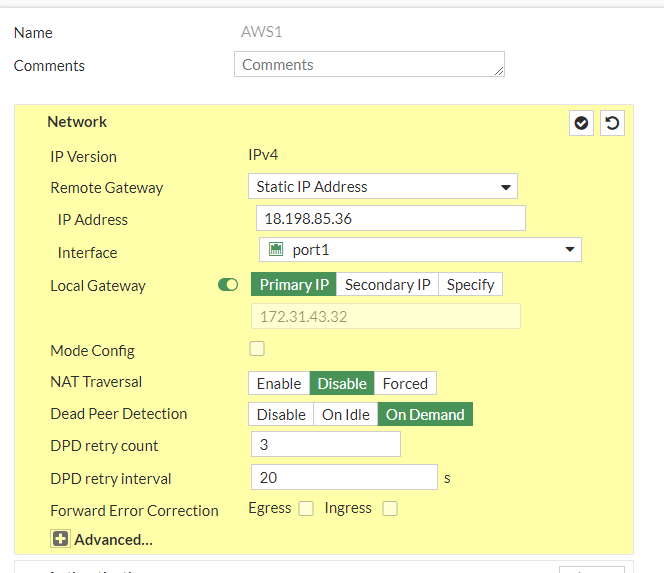
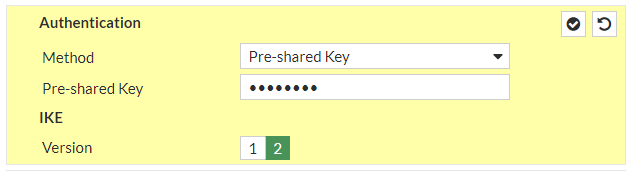
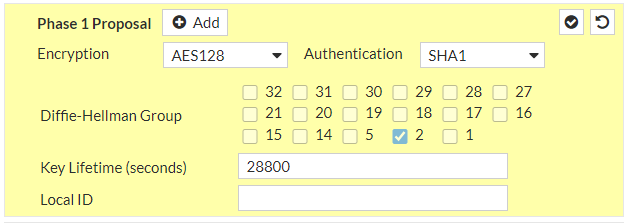
and continue with #2: IPSec Configuration
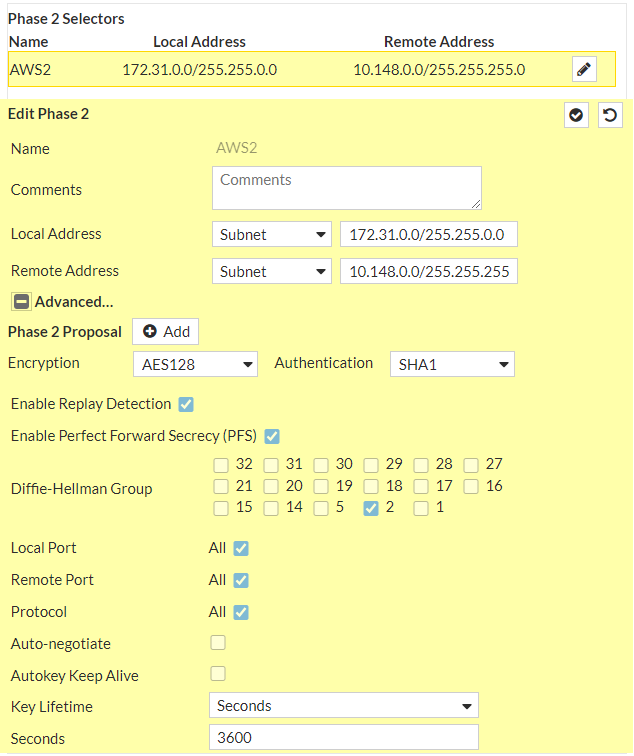
Under Phase 2 Selectors --> New Phase 2a. Name: vpn-0363a544a262b4880-0b. Local Address: LAN subnet behind Fortigate/0.0.0.0/0c. Remote Address: AWS Private Subnet/0.0.0.0/0Under Advancedd. Encryption: aes128e. Authentication: sha1f. Select Enable Replay Detectiong. Select Perfect Forward Secrecyh. DH Group: 2 ! and deselect 5i. Keylife: 3600 secondsj. Enable Auto-negotiate ! Autokey Keep Alive is enabled automatically when Auto-negotiate is enabledk. Click Ok
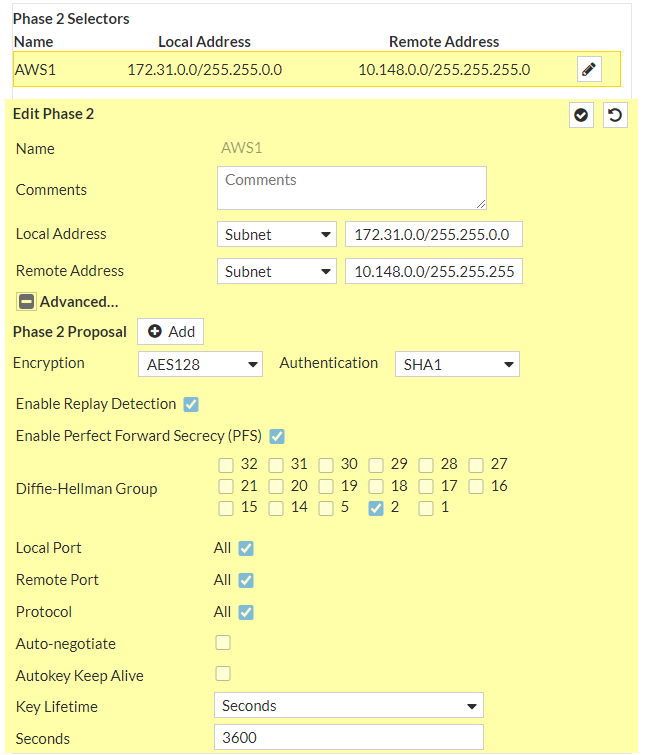
and let’s do the same also for the IPSec Tunnel #2
Under “Network” Section:a. IP Version: IPv4b. Remote Gateway: Static IP Addressc. IP address: 52.29.221.101d. Local Interface: wan1e. Local Gateway: Select Specify and enter WAN port IP (Public IP)f. Dead Peer Detection: Enable by selecting On Idle/ On Demandg. Authentication Method: Pre-shared Keyh. Pre-Shared Key: gKHDaXqdxKODpngoJdGIS4.T2KLS2enzi. IKE Version: 2Phase 1 Proposal:j. Encryption: aes128k. Authentication: sha1l. DH group: 2 ! and deselect 5m. Keylife: 28800 seconds
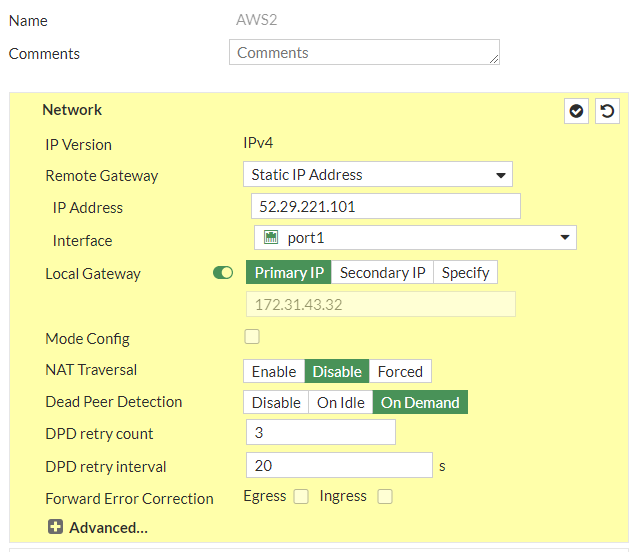
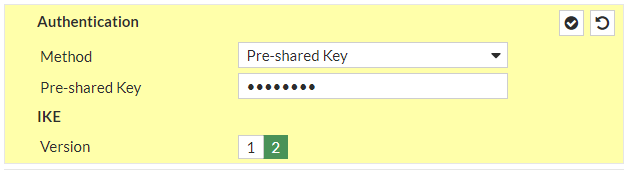
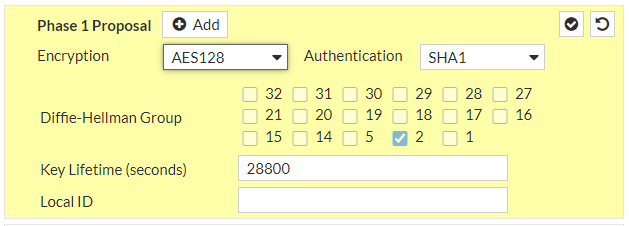
and
Under Phase 2 Selectors --> New Phase 2a. Name: vpn-0363a544a262b4880-1b. Local Address: LAN subnet behind Fortigate/0.0.0.0/0c. Remote Address: AWS Private Subnet/0.0.0.0/0Under Advancedd. Encryption: aes128e. Authentication: sha1f. Select Enable Replay Detectiong. Select Perfect Forward Secrecyh. DH Group: 2 ! and deselect 5i. Keylife: 3600 secondsj. Enable Auto-negotiate ! Autokey Keep Alive is enabled automatically when Auto-negotiate is enabledk. Click Ok
Configure Tunnel interfaces
A tunnel interface is configured to be the logical interface associated with the tunnel.
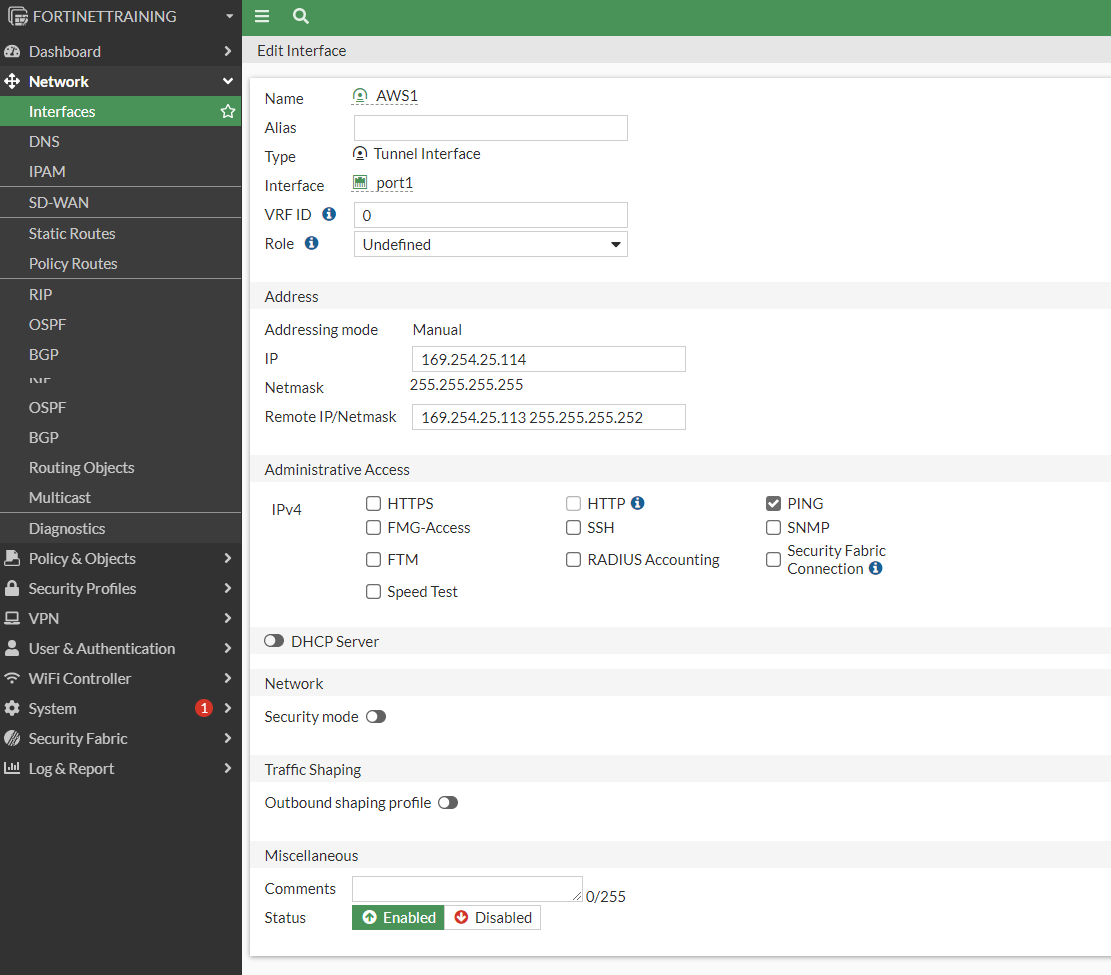
As defined in #3: Tunnel Interface Configuration we should configure the addresses accordingly:
a. IP : 169.254.25.114b. Remote IP: 169.254.25.113/30c. Select Pingd. Administrative Status: Upe. Select Ok.
Go to Networks > Interfaces > expand the physical interface attached to the tunnel interfaces and click on those tunnel interfaces:
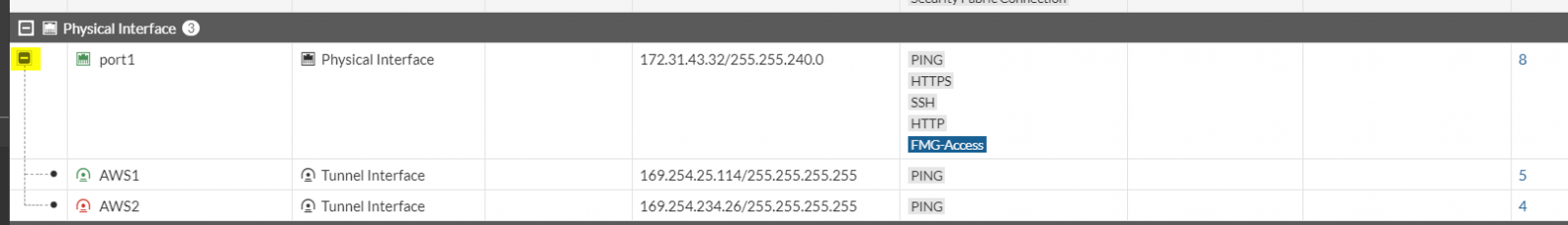
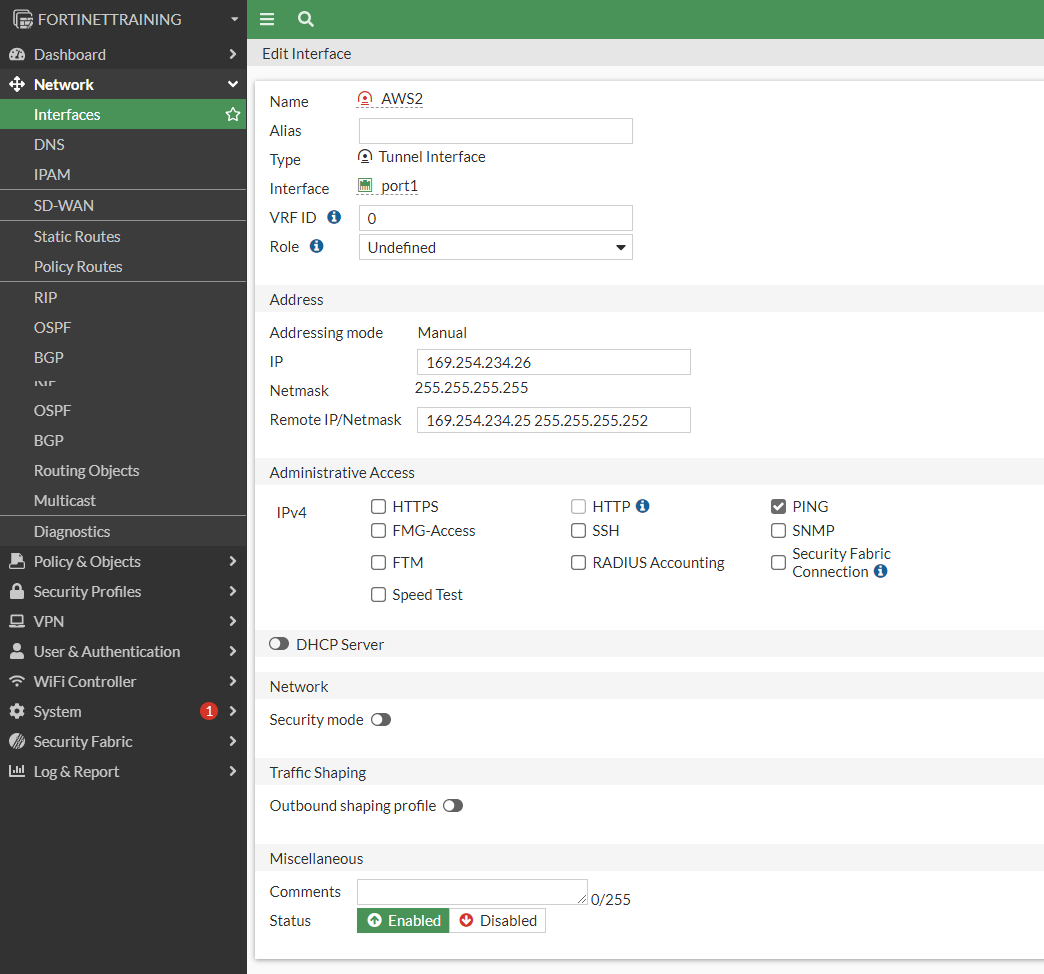
do the same for the second interface:
a. IP : 169.254.234.26b. Remote IP: 169.254.234.25/30c. Select Pingd. Administrative Status: Upe. Select Ok.
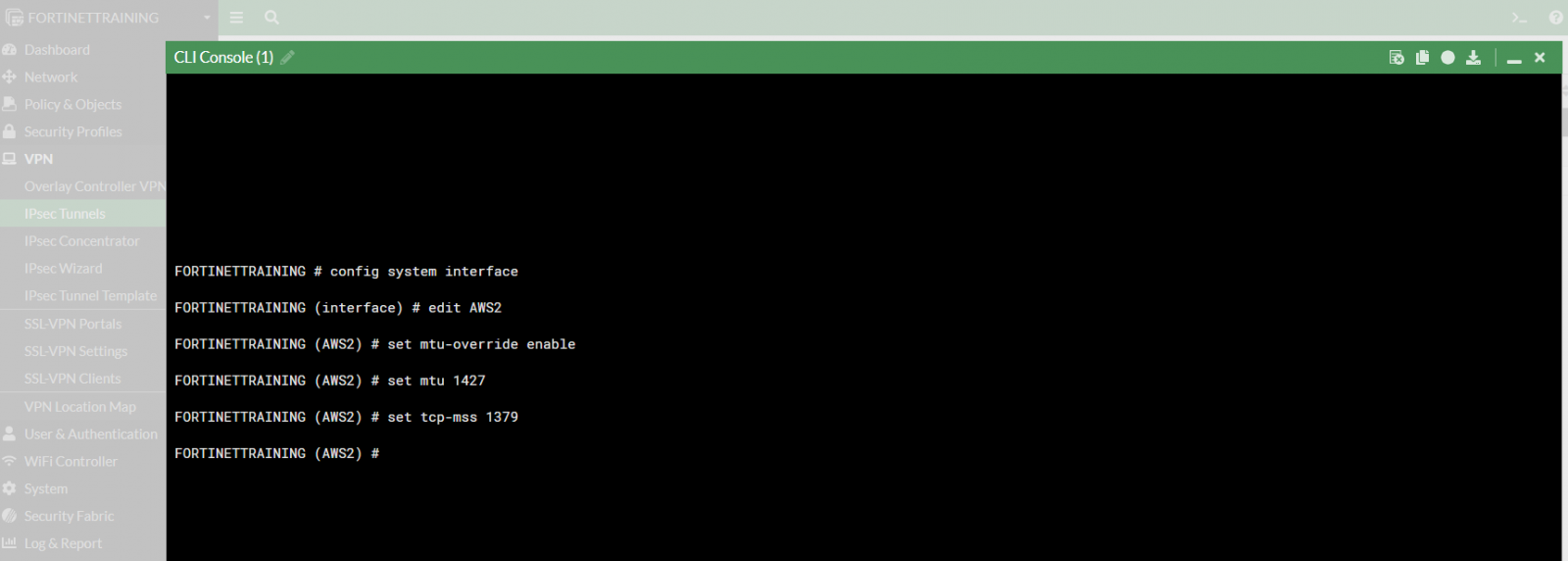
To set the MTU and MSS as reported in the template conf:
!You can set MTU and MSS on the tunnel by performing this from the CLI: config global config system interface edit "vpn-0363a544a262b4880-1" ! This name will be the same as the VPN tunnel name set mtu-override enable set mtu 1427 set tcp-mss 1379 nextend
Open the CLI Console
and configure both interfaces (AWS1 and AWS2):
Configure Static Routes
Configure static routes to route VPC network over the tunnel interfaces.
Go to Network > Static Routes and create:
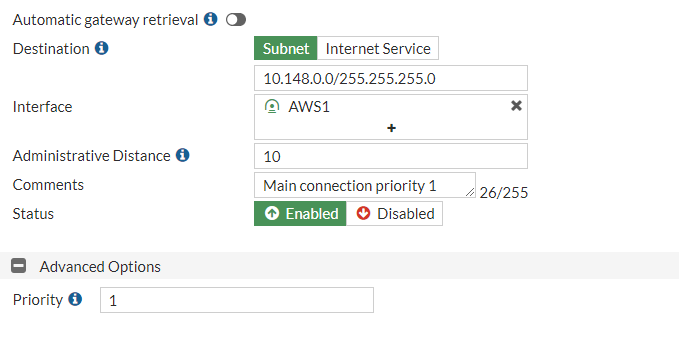
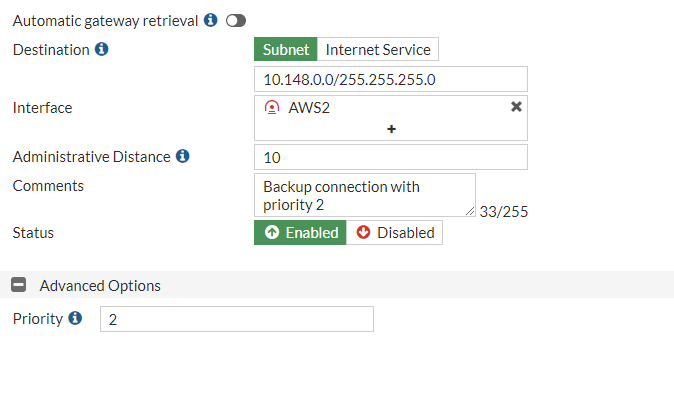
We setup the two routes with the same “Distance” but different “Priority” for failover of traffic between tunnels like explained hereunder.
VPN Monitor
AWS configuration wants to have 2 VPN tunnels active.
The issue in having 2 VPN tunnels active is that the control of sessions can get very messed up or you drop packets because of the stateful operation of the Fortigate firewall.
There are at least 2 ways to do this: using VPN monitoring with static routing or via BGP.
In this static configuration we need to configure VPN monitoring.
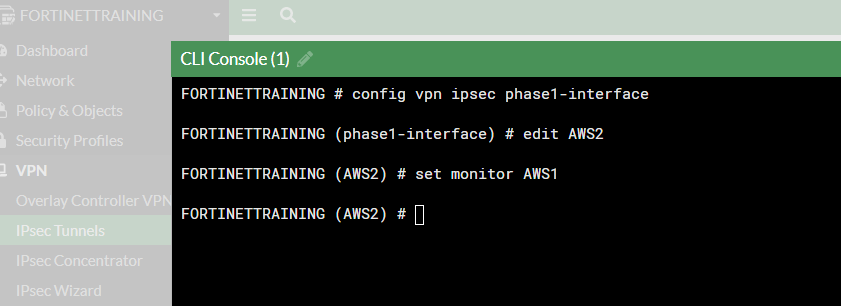
It’s very simple: just edit the secondary tunnel interface and set as monitor the primary tunnel interface, so that we have a failover of traffic between tunnels:
config vpn ipsec phase1-interface edit "secondary-tunnel-interface" set monitor "primary-tunnel-interface" nextend
Using the CLI Console in our example:
Configure Firewall policies
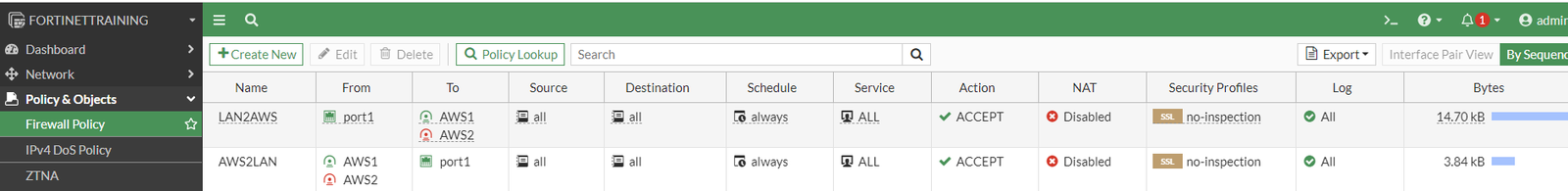
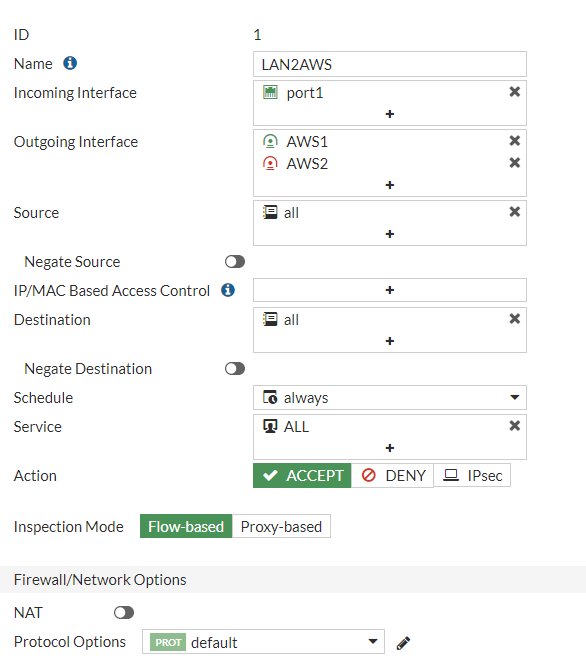
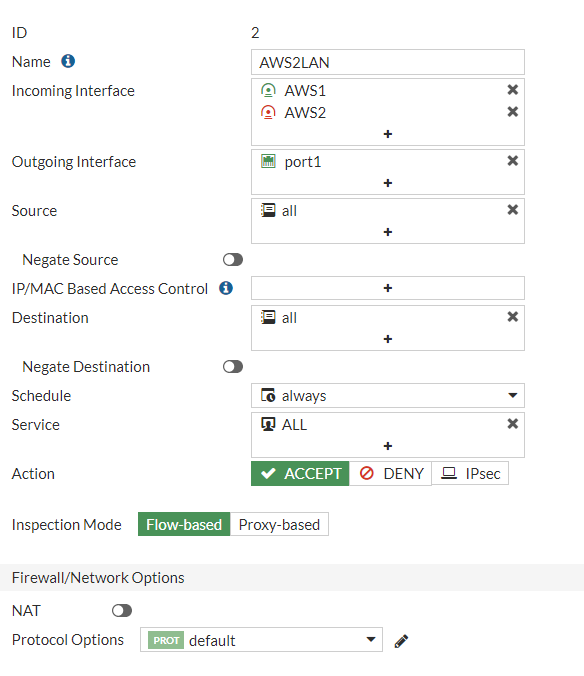
We need to create at least two firewall policies permitting traffic from local network to VPN subnet and vice versa:
Testing
Going back to VPN > IPsec Tunnels we should be able to see the primary tunnel up and the secondary tunnel “inactive”:
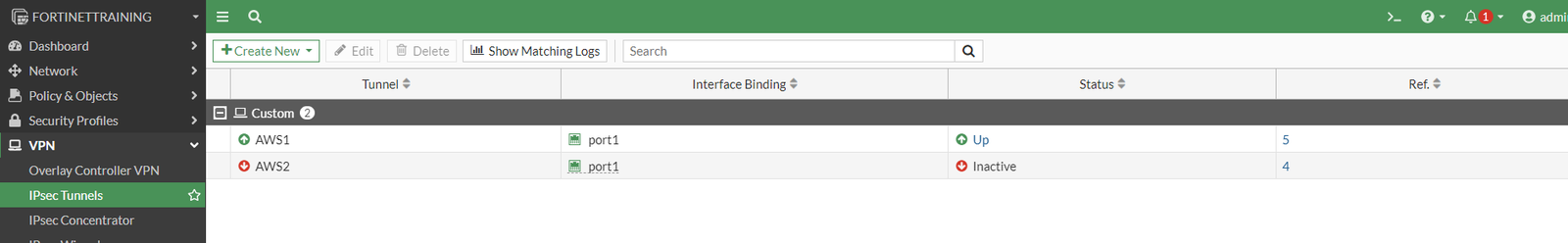
Increase the security in the VPN connection
Now, since AWS side VPN tunnels support better security, we can adjust Fortinet configuration accordingly. We can use:
AES256 instead of AES128
SHA-256 instead of SHA1
Diffie-Hellman group >21 (up to 24) instead of DH2
FortiOS 7.2 supports DH32, but we should use latest version supported by both sides, namely DH21
Let’s adjust Fortinet configuration:
VPN > IPsec Tunnels > edit both tunnels with the new parameters:
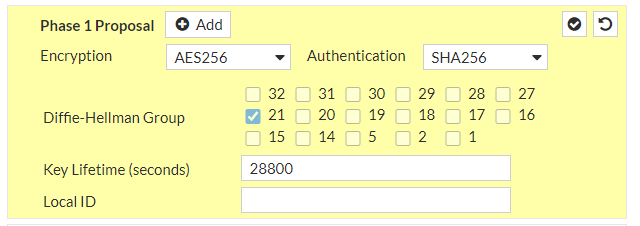
and
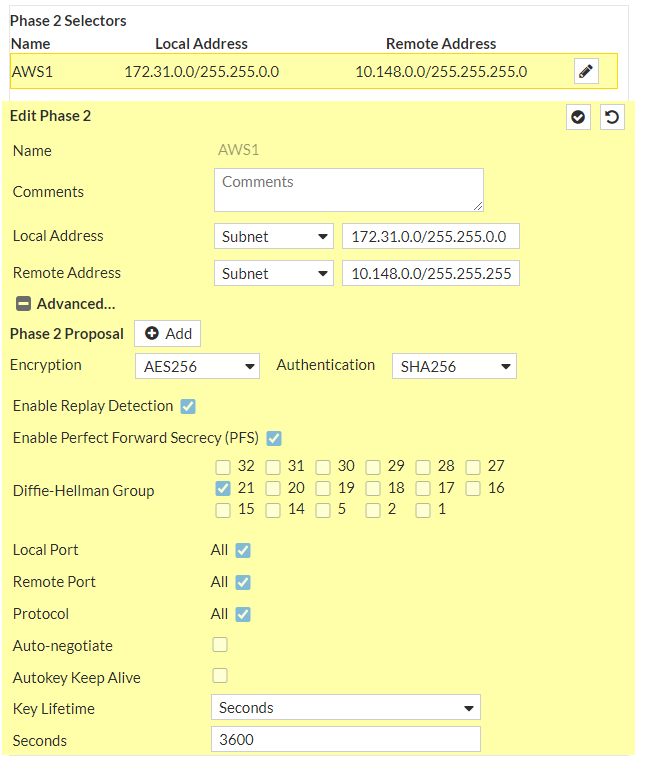
Now the IPSec tunnels will be up and running with maximum security:
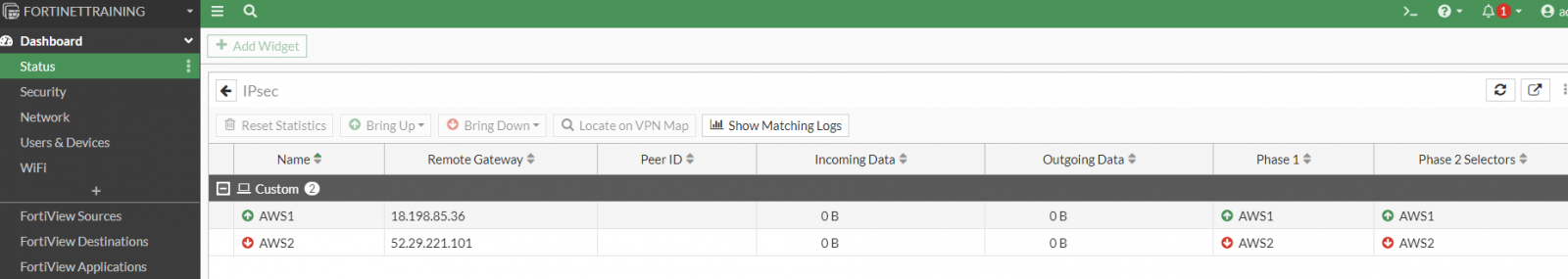
We have done!
For more information and support please contact our UCCS Onboarding Team.
