Sophos XG V19+ ikev2 (dynamic)
Configuring Sophos Next Generation Firewall
Tested Version: Sophos XG version 19
In this section we will refer to the configuration file you can download from AWS as “template conf” and will explain how to use its contents for configuring Sophos XG V19
As a reference for this guide, you can find here the full AWS file: Sophos XG V19+ ikev2 (dynamic).txt
Create VPN Tunnels
Open the web interface of the firewall and move to Site-to-site VPN > Amazon VPC > Amazon VPC connection setup:
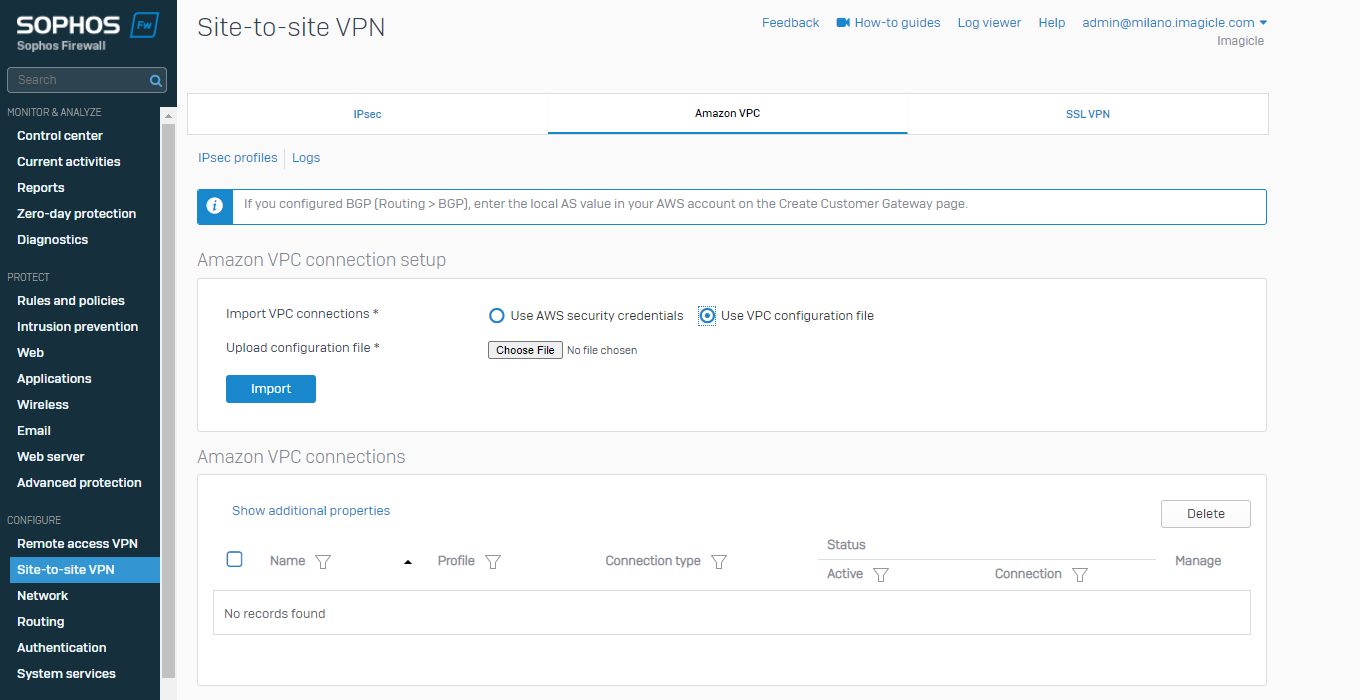
Select “Use VPC configuration file” and upload the configuration file in “Choose File”
After few minutes you should be able to see both tunnel up and running:
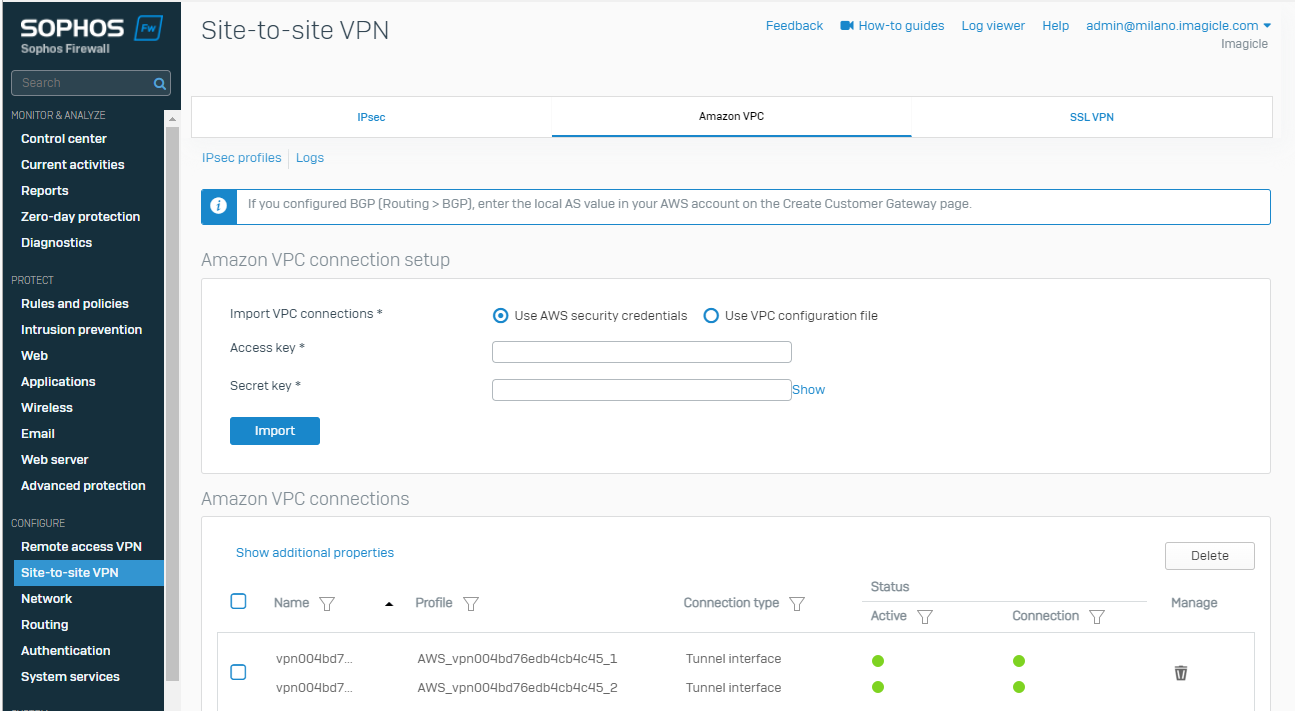
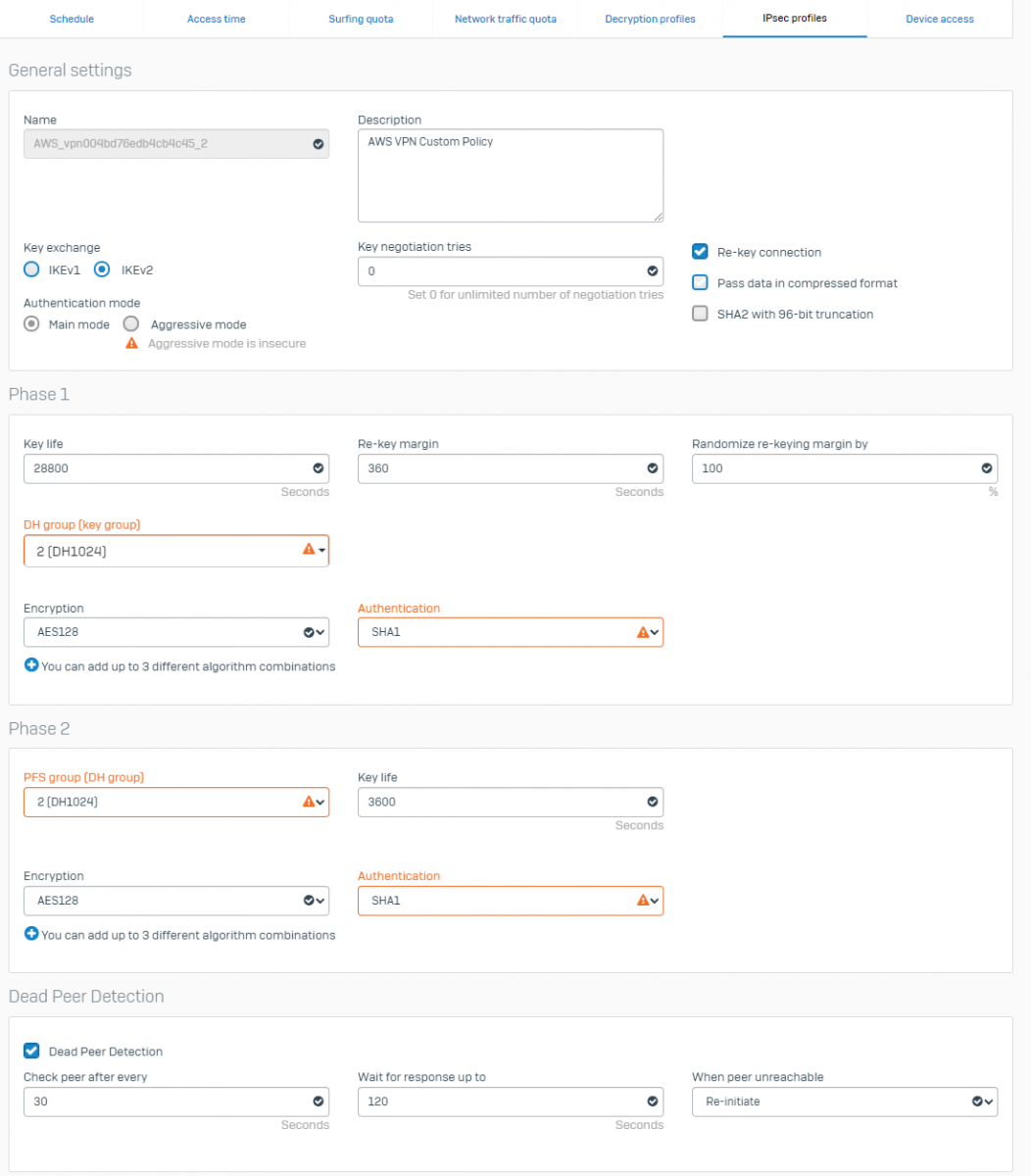
Go to System > Profiles > IPsec profiles to view the VPN Policy of Internet Key Exchange (IKE) as the conf template
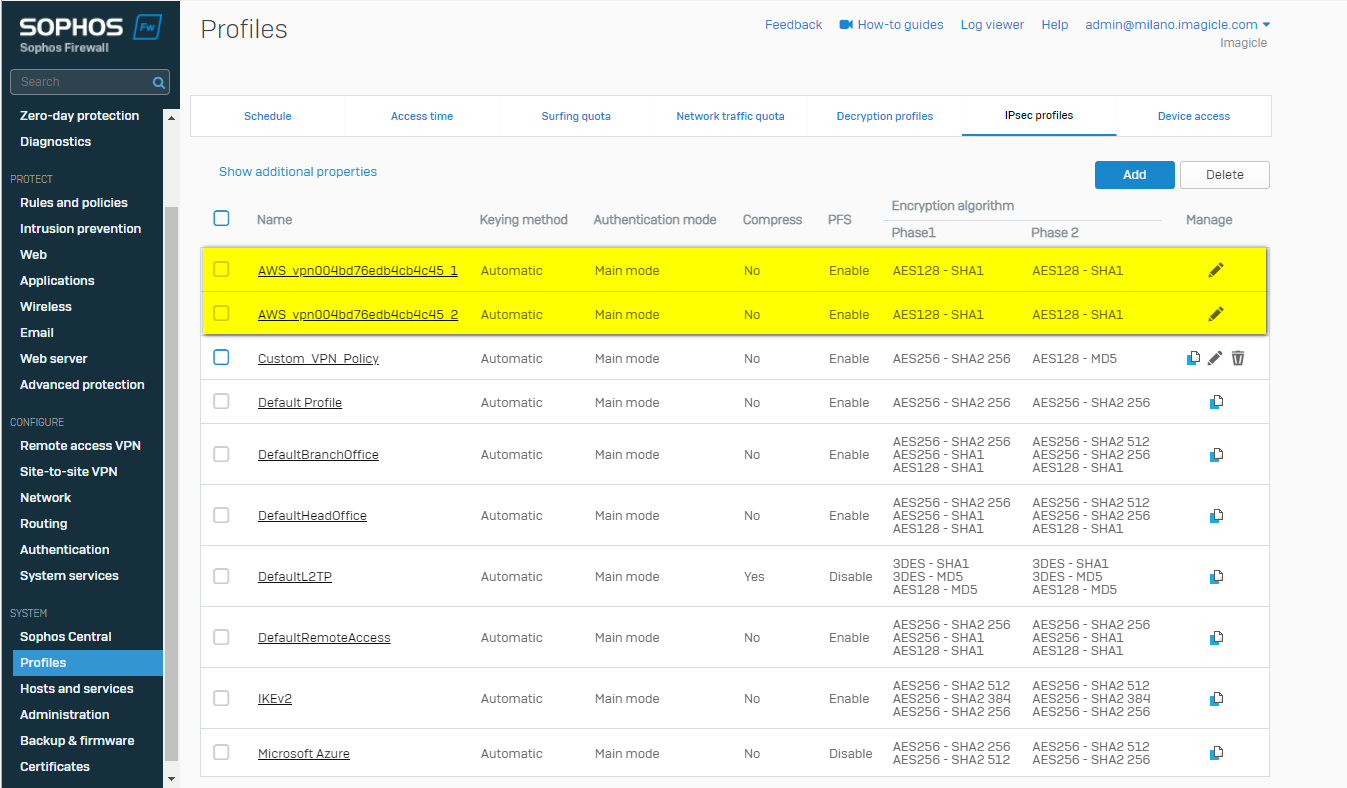
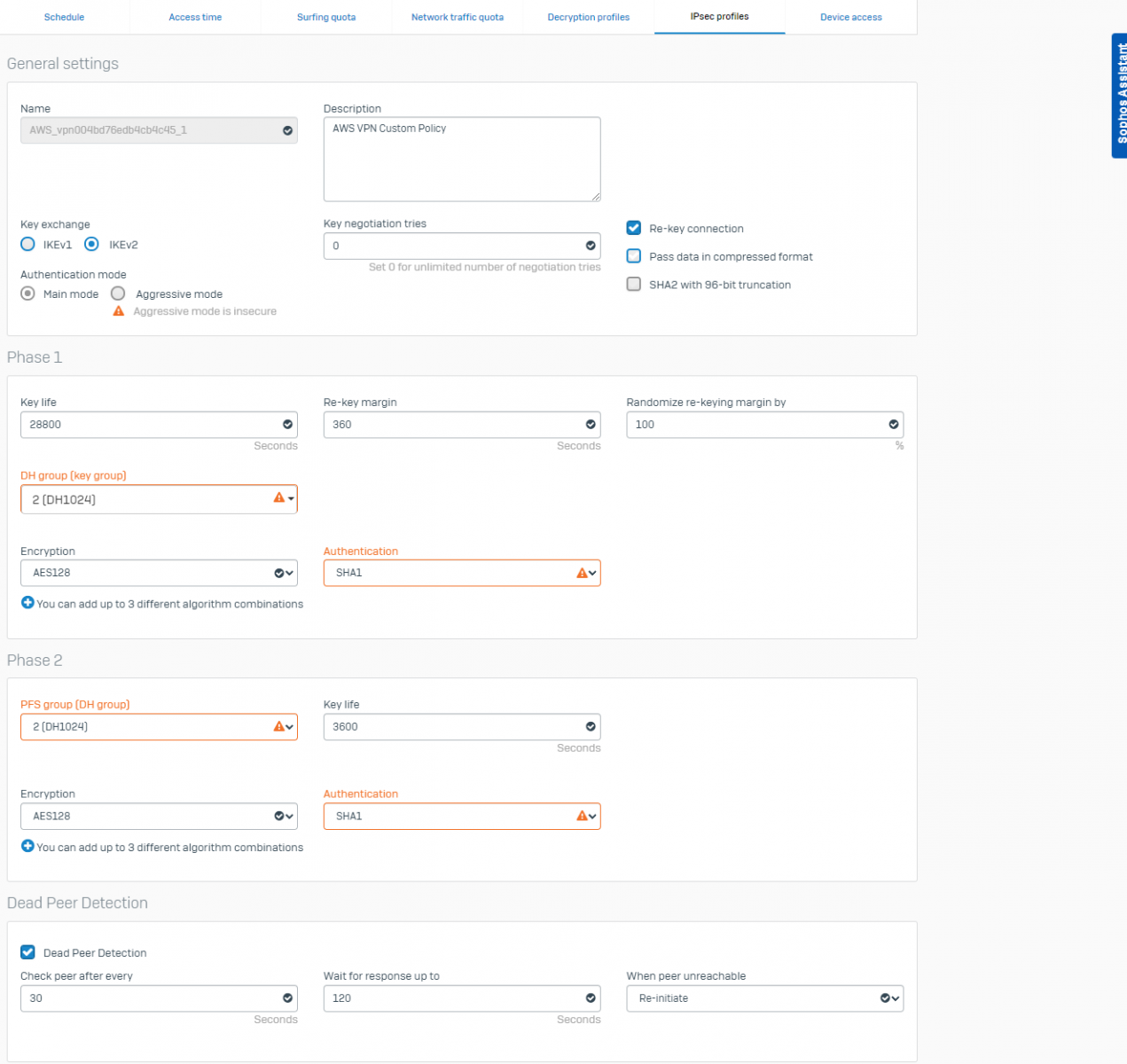
Tunnel 1
<ike> <authtype>psk</authtype> <authentication_protocol>sha1</authentication_protocol> <encryption_protocol>aes-128-cbc</encryption_protocol> <lifetime>28800</lifetime> <perfect_forward_secrecy>group2</perfect_forward_secrecy> <mode>main</mode> <pre_shared_key>45yRVCcBqc6Gr0umXrSrBxshu3YaQone</pre_shared_key></ike><ipsec> <key_exchange>ikev2</key_exchange> <protocol>esp</protocol> <authentication_protocol>hmac-sha1-96</authentication_protocol> <encryption_protocol>aes-128-cbc</encryption_protocol> <lifetime>3600</lifetime> <perfect_forward_secrecy>group2</perfect_forward_secrecy> <mode>tunnel</mode> <clear_df_bit>true</clear_df_bit> <fragmentation_before_encryption>true</fragmentation_before_encryption> <tcp_mss_adjustment>1379</tcp_mss_adjustment> <dead_peer_detection> <interval>10</interval> <retries>3</retries> </dead_peer_detection> </ipsec>
Tunnel 2
<ike> <authtype>psk</authtype> <authentication_protocol>sha1</authentication_protocol> <encryption_protocol>aes-128-cbc</encryption_protocol> <lifetime>28800</lifetime> <perfect_forward_secrecy>group2</perfect_forward_secrecy> <mode>main</mode> <pre_shared_key>MoKSN15pp0xVId2Vnk_3hYJildOI.7mf</pre_shared_key></ike><ipsec> <key_exchange>ikev2</key_exchange> <protocol>esp</protocol> <authentication_protocol>hmac-sha1-96</authentication_protocol> <encryption_protocol>aes-128-cbc</encryption_protocol> <lifetime>3600</lifetime> <perfect_forward_secrecy>group2</perfect_forward_secrecy> <mode>tunnel</mode> <clear_df_bit>true</clear_df_bit> <fragmentation_before_encryption>true</fragmentation_before_encryption> <tcp_mss_adjustment>1379</tcp_mss_adjustment> <dead_peer_detection> <interval>10</interval> <retries>3</retries> </dead_peer_detection></ipsec>
Configure BGP
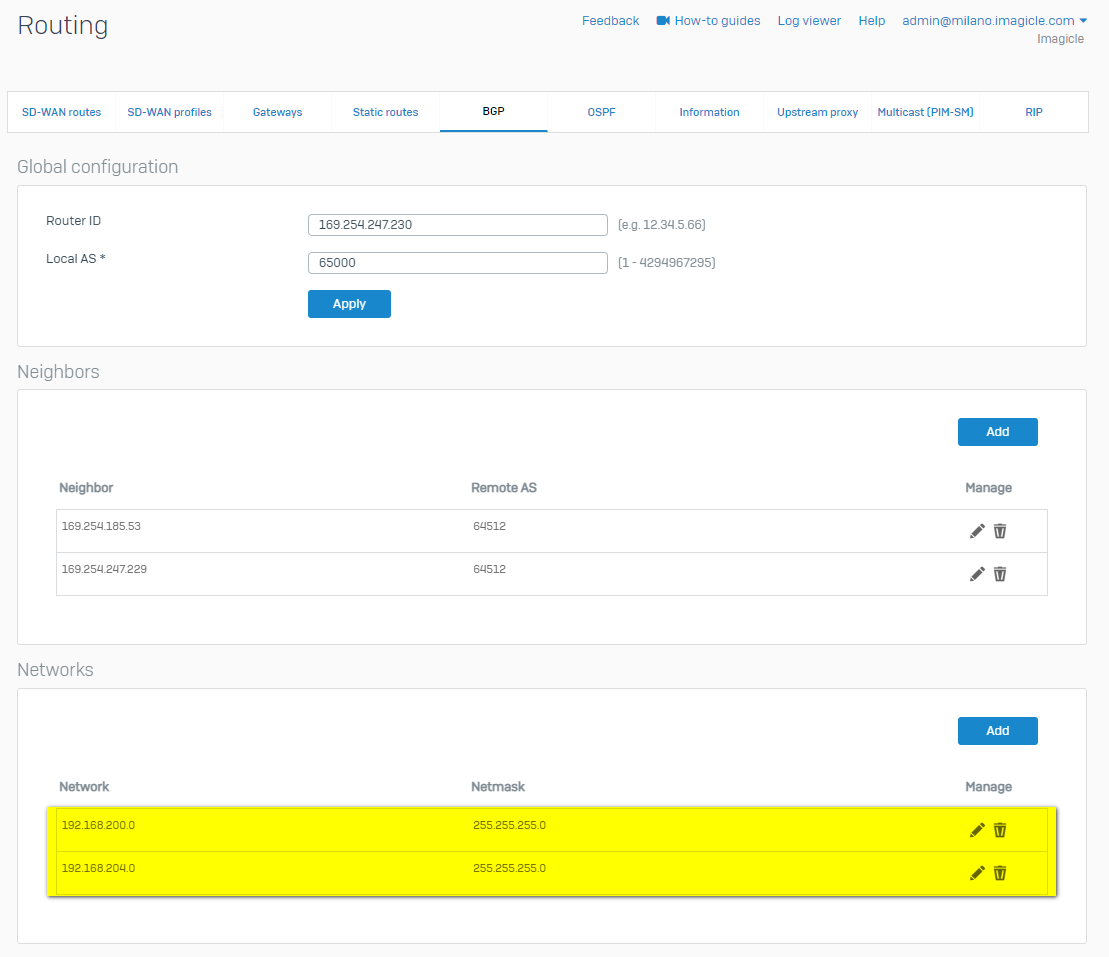
In Configure > Routing |> BGP it’s showed the configuration of BGP as the conf template:
<bgp> <asn>65000</asn> <hold_time>30</hold_time></bgp><tunnel_inside_address> <ip_address>169.254.185.53</ip_address> <network_mask>255.255.255.252</network_mask> <network_cidr>30</network_cidr></tunnel_inside_address><tunnel_inside_address> <ip_address>169.254.247.229</ip_address> <network_mask>255.255.255.252</network_mask> <network_cidr>30</network_cidr></tunnel_inside_address>
To establish BGP routes between your network and Amazon VPC, you must add the local subnet to your BGP networks.
Go to Routing > BGP > Networks, click Add and insert you local network
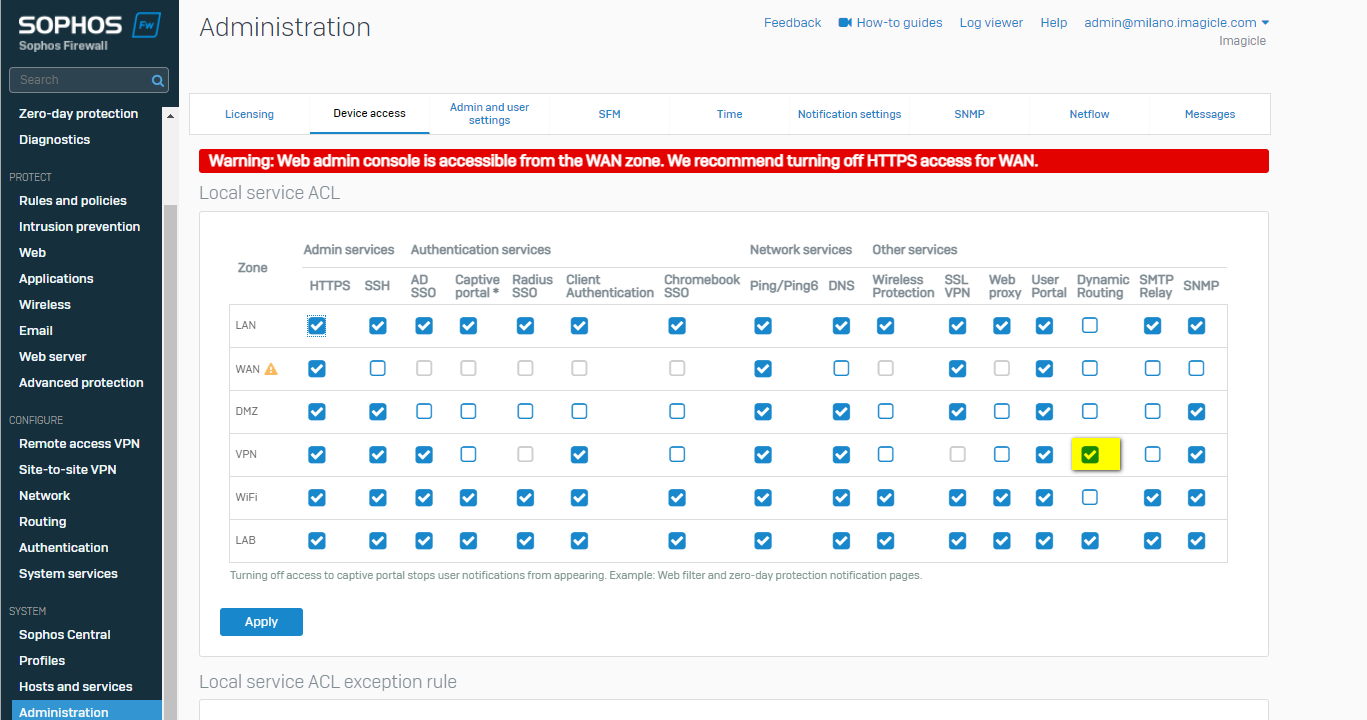
You must enable the dynamic routing for the VPN zone for Sophos Firewall to use BGP routing with Amazon VPC.
Go to Administration > Device Access and enable Dynamic Routing for the VPN zone.
Create firewall rules for VPN traffic
You must create outbound and inbound firewall rules to allow traffic between your local network and Amazon VPC.
To create a firewall rule for outbound VPN traffic, go to Rules and policies > Firewall rules > Add firewall rule, and click New firewall rule.
In this case the Amazon VPC Networks is 10.148.0.0/16
To check the status of BGP and Routing go to Routing > Information > BGP
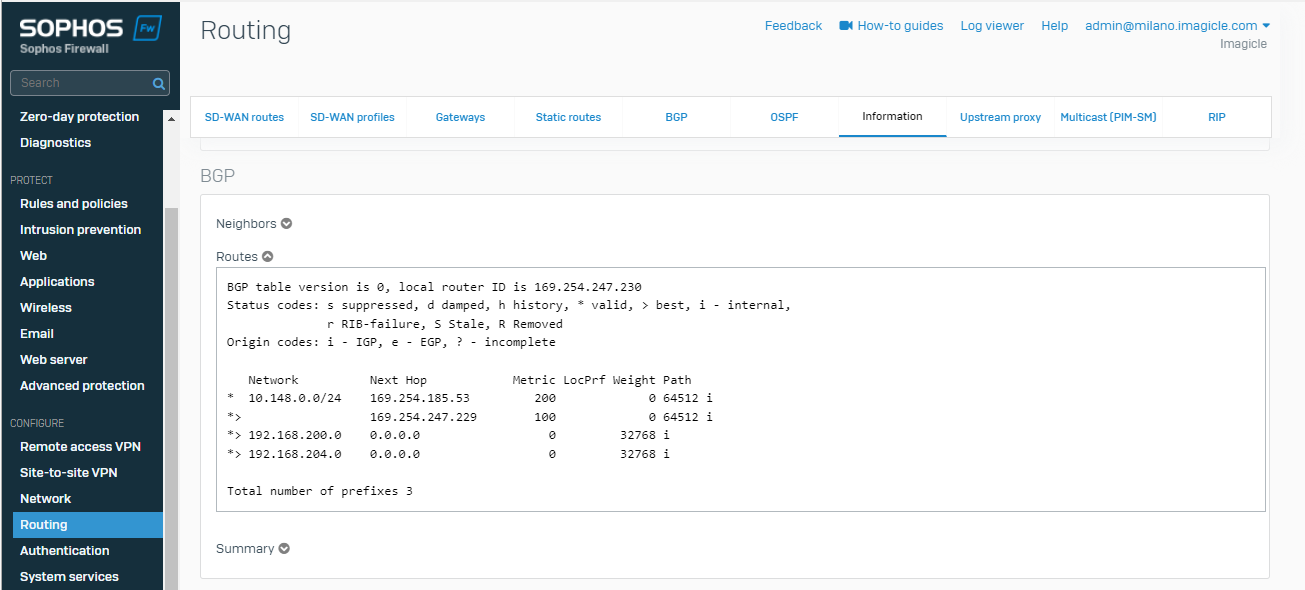
Testing
Going back Site-to-site VPN > Amazon VPC >Amazon VPC connection we should be able to see both tunnels up:
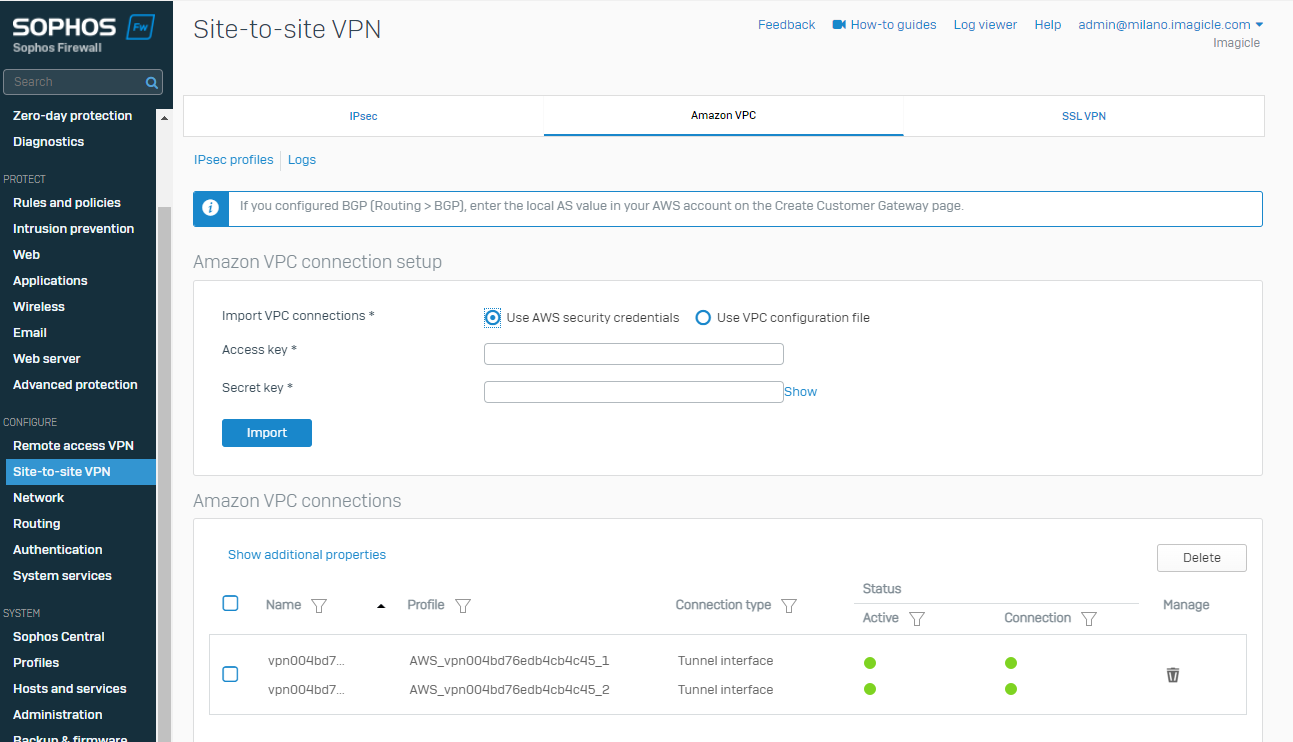
Increase the security in the VPN connection
Now, since AWS side VPN tunnels support better security, we can adjust Sophos configuration accordingly.
So we can use:
AES-256 instead of AES-128
SHA512 instead of SHA1
Diffie-Hellman group 18 instead of DH 2, Sophos supports DH18
IKEv2 whenever possible
Let’s adjust Sophos configuration:
Go to System > Profiles > IPsec profiles > edit both tunnels with the new parameters:
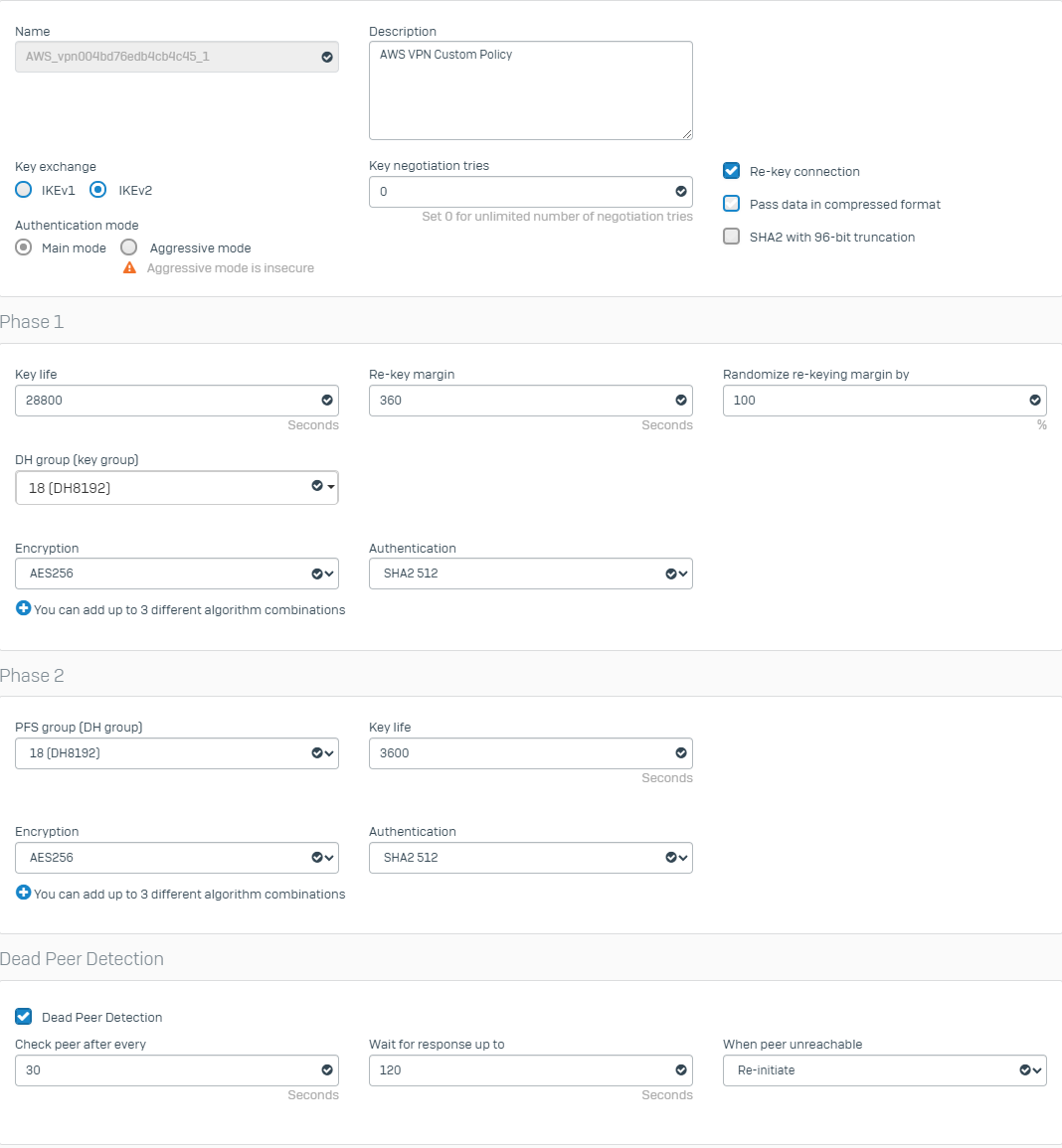
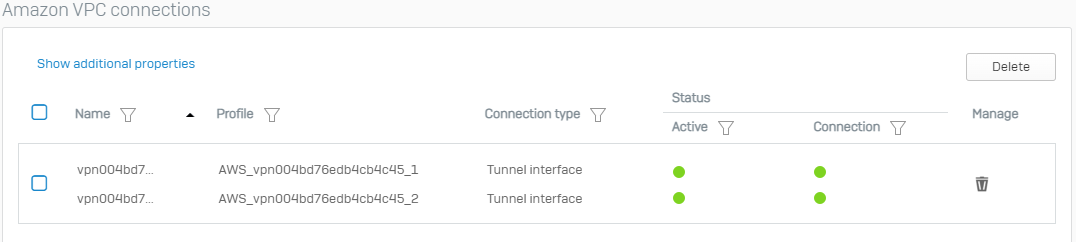
Now the IPSec tunnels will be up and running with maximum security:
We have done!
For more information and support please contact our UCCS Onboarding Team
