Configure Cisco ECC to use HTTPS
Applies to:
Imagicle UCX Suite for Cisco UC, rel. Summer 2017 or newer
Description:
This article details how to configure CuCM and UCX Suite to use HTTPS for ECC-Curri.
Curri can be used with several UCX Suite applications: Phone Lock, Contact Manager Lookup and/or SmartNumbers, Call Recording announcement.
How-to:
Requirements
On CuCM, the DNS must be correctly configured to resolve UCX Suite server(s) FQDN.
When the UCX Suite server is joined to a domain, the Active Directory will try to register the UCX Suite computer name in the company DNS. Hence, every server should be able to resolve the UCX Suite server name. If this is not the case, you must add a static entry in the company DNS to let the CUCM reach the UCX Suite server using its name (fqdn).
1. Configure the External Call Control Profile for HTTPS
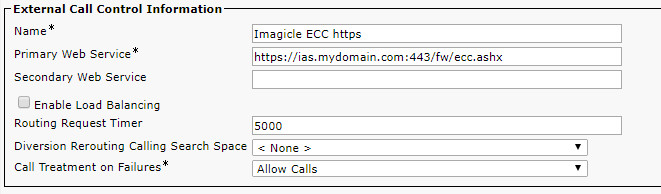
In the Primary Web Service field of the ECC profile, enter the UCX Suite web service URL, e.g. https://UCX Suite.mydomain.com:443/fw/ecc.ashx.
Notes:
a. https://UCXSuite.mydomain.com:443/fw/ecc.ashx
In the address remember to specify the port :443. The port number must be explicitly written even if implied by the https protocol.
b. https://UCXSuite.mydomain.com:443/fw/ecc.ashx
In the address you must use the netbios computer name (UCXSuite.mydomain.com), not the IP address.
It must be the same name specified in the Common Name of the SSL certificate (CN value)
2. Adjust the Certificate on the UCX Suite server
The Common Name (CN) field of the certificate used by IIS must contain the machine Fully Qualified Domain Name used in the External Call Control profile URL.
To ensure this, different steps has to be followed depending on whether the customer has a certificate issued by a trusted Certificate Authority (CA), trusted by the Domain Controller, or wants to use a self-signed certificate.
The procedure is detailed here.
3. Import certificate(s) into CUCM
In order to let CUCM trust the HTTPS connection, the certificate chain configured on UCX Suite web server must be imported into all CUCM nodes.
Actually, there are two possible scenarios:
The Imagicle WEB server runs a self-signed certificate. In this case you need to import into CUCM the self-signed certificate, as described below.
The Imagicle WEB server runs a signed certificate issued by an internal/external CA (certificate authority). In this case you need to import into CUCM the certificates of the Root CA and of any intermediate CA appearing in the certificate chain. You don't need to import the server certificate, instead.
NOTE: the following procedure and screenshots describe the first case (self-signed certificate), but the same steps apply also to the second case, for the CA certifcates.
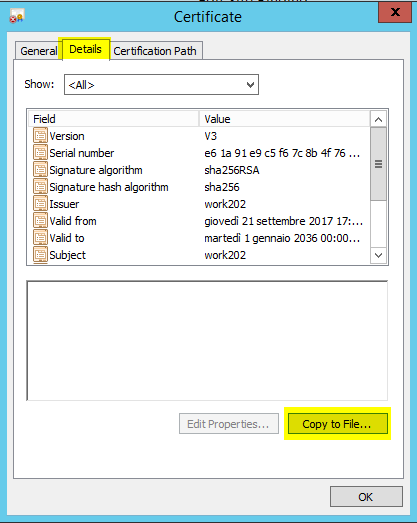
a. Export the Certificate used by Application Suite web server
In "Server Certificates" section of "Internet Information Services (IIS) Manager", double click on the certificate used by the binding on port 443 (see previous paragraph). Click on "Details" tab and then click on "Copy to File.." button.
The Certificate Export Wizard will start, click Next. Choose "No, do not export private key".
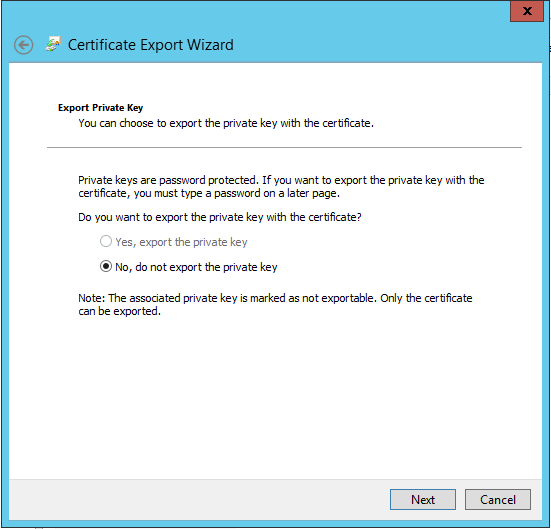
Choose to export certificate in "DER encoded binary X.509 (CER)" format.
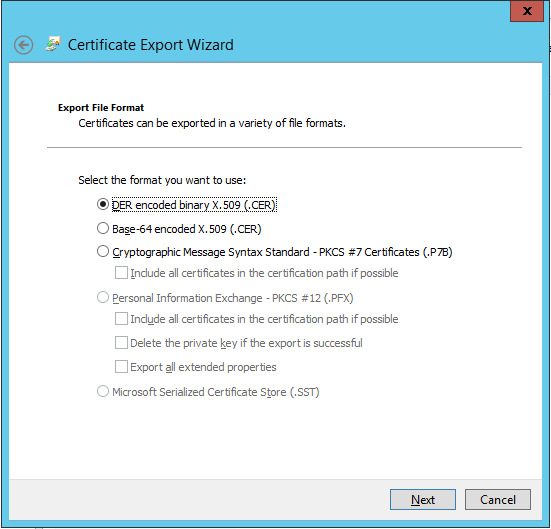
Then complete the wizard, it will save a .cer file.
b. Load certificate(s) to CUCM
The certificates must be loaded on all CUCM nodes. Since CUCM 8.5, they're expected to be automatically replicated among cluster nodes.
Login into "Cisco Unified OS Administration", and go to "Security", "Certificate Management".
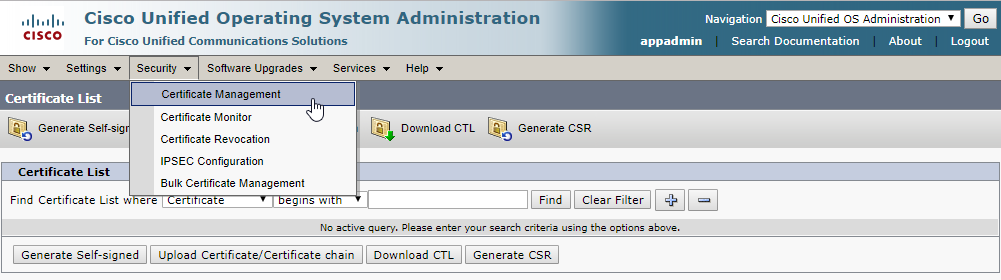
Then click on "Upload Certificate/Certificate chain"
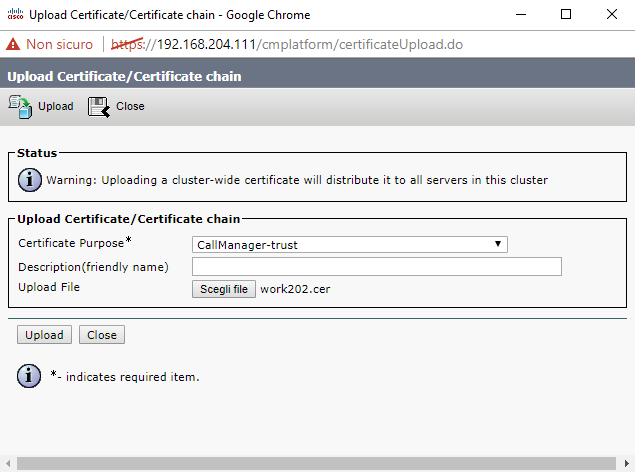
In the upload form, choose "CallManager-trust" as Certificate purpose, then select the .cer file and upload it.
Go to "Certificate Management" of each CUCM node to check that certificate has been properly replicated.
For HA installations, please repeat above procedure for each Imagicle node.
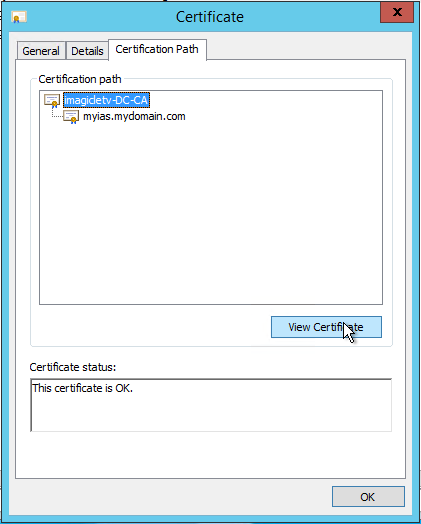
Troubleshooting: check certificates trust chain
In order to let CUCM trust the HTTPS connection established with UCX Suite web server, CUCM must also know all the certificates in UCX Suite certificate's certification path.
In "Server Certificates" section of "Internet Information Services (IIS) Manager", double click on the certificate used by the binding on port 443.
Click on "Certification Path" tab: CUCM must be able to verify every certificate displayed in this panel. So, in CUCM, go to "Certificate Management" and check that appropriate entries exist with "CallManager-trust" as Certificate purpose.
If not, select the missing certificate in the "Certification path" panel, export and upload it to CUCM as explained in step 3b.